Several websites, that are hosted on servers I manage, recently fell victim to XML Quadratic Blowup Attacks. They were all running WordPress version 3.9.1 or below.
I first noticed a problem when one of the servers started to run extremely slowly. Every website it hosted was taking an age to respond and frequently timing out. The CPU was maxed out at 100%, mainly from PHP requests.
Further investigation narrowed down the website under attack. Below is a screenshot showing the traffic trend for the month to date of that website.
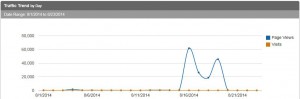
On 15th August page views began to spike, with the most popular requested file being xmlrpc.php.
The temporary fix was to rename the file before installing WordPress 3.9.2, which contains a fix for this exploit.
However, I began to wonder how many other sites, that I was responsible for, could be vulnerable.
So, I decided to write a PowerShell script that scans all websites (on IIS 6 or 7) and checks their current WordPress installation version.
Since the WordPress API is used to obtain the current version, you can set this script to run as a task on your server. If an out of date installation of WordPress is detected then you’ll receive an email notification.
To turn on email updates, set $SendEmail (line 5) to 1 and be sure to update lines 6 – 11 with your email address and SMTP server details.